CentOS 7에서 Docker와 함께 Ansible AWX를 설치하는 방법
이 페이지에서
- AWX 서버의 시스템 요구 사항\n
- AWX 서버에서 비밀번호 없는 로그인 구성\n
- 참조
Ansible AWX는 ansible tower의 OpenSource 버전입니다. AWX는 Ansible 위에 구축된 웹 기반 사용자 인터페이스, REST API 및 작업 엔진을 제공합니다. AWX의 상업적 파생물인 Tower의 업스트림 프로젝트입니다.
이 자습서에서는 Docker를 사용하여 AWX를 설치하고 구성하는 방법을 보여줍니다.
나는 centos 7 최소 설치와 허용 모드에서 SELinux로 3개의 서버를 사용할 것입니다.
- 192.168.1.25 AWX 서버
- 192.168.1.21 클라이언트1
- 192.168.1.22 클라이언트2
AWX 서버의 시스템 요구 사항
- 최소 4GB의 메모리.
- 적어도 2개의 cpu 코어.
- 최소 20GB의 공간.
- Docker, Openshift 또는 Kubernetes 실행.\n
SELinux 구성을 확인하십시오.
sestatus
결과:
[ ~]# sestatus SELinux status: enabled SELinuxfs mount: /sys/fs/selinux SELinux root directory: /etc/selinux Loaded policy name: targeted Current mode: permissive Mode from config file: permissive Policy MLS status: enabled Policy deny_unknown status: allowed Max kernel policy version: 28 [ ~]#
방화벽을 비활성화합니다.
[ installer]# systemctl stop firewalld [ installer]# systemctl disable firewalld Removed symlink /etc/systemd/system/multi-user.target.wants/firewalld.service. Removed symlink /etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service. [ installer]#
/etc/hosts에 호스트 항목 추가
[ ~]# cat /etc/hosts 192.168.1.25 awx.sunil.cc awx 192.168.1.21 client1.sunil.cc client1 192.168.1.22 client2.sunil.cc client2 [ ~]#
epel 저장소를 활성화합니다.
[ ~]# yum install -y epel-release
패키지를 설치합니다.
[ ~]# yum install -y yum-utils device-mapper-persistent-data lvm2 ansible git python-devel python-pip python-docker-py vim-enhanced
docker ce 안정 리포지토리를 구성합니다.
[ ~]# yum-config-manager --add-repo https://download.docker.com/linux/centos/docker-ce.repo
도커 설치.
[ ~]# yum install docker-ce -y
도커 서비스를 시작합니다.
[ ~]# systemctl start docker
도커 서비스를 활성화합니다.
[ ~]# systemctl enable docker
AWX 저장소를 복제합니다.
[ ~]# git clone https://github.com/ansible/awx.git [ ~]# cd awx/ [ awx]# git clone https://github.com/ansible/awx-logos.git [ awx]# pwd /root/awx [ awx]#
/root/awx 내의 설치 프로그램 디렉토리로 이동합니다.
[ awx]# cd installer/
인벤토리에서 다음 매개변수를 수정합니다.
[ awx]# vim inventory postgres_data_dir=/var/lib/pgdocker awx_official=true awx_alternate_dns_servers="4.2.2.1,4.2.2.2" project_data_dir=/var/lib/awx/projects
구성은 다음과 같아야 합니다.
[ installer]# cat inventory |grep -v "#" localhost ansible_connection=local ansible_python_interpreter="/usr/bin/env python" [all:vars] dockerhub_base=ansible dockerhub_version=latest rabbitmq_version=3.6.14 awx_secret_key=awxsecret postgres_data_dir=/var/lib/pgdocker host_port=80 docker_compose_dir=/var/lib/awx pg_username=awx pg_password=awxpass pg_database=awx pg_port=5432 awx_official=true awx_alternate_dns_servers="4.2.2.1,4.2.2.2" project_data_dir=/var/lib/awx/projects [ installer]#
이제 Docker를 통해 AWX를 배포합니다.
[ installer]# ansible-playbook -i inventory install.yml -vv
이 작업은 서버 구성에 따라 다소 시간이 걸립니다.
AWX용 ansible play 배포를 확인하려면 아래 명령을 실행합니다.
[ installer]# docker container ls CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 318c7c95dcbb ansible/awx_task:latest "/tini -- /bin/sh -c." 12 minutes ago Up 12 minutes 8052/tcp awx_task 642c2f272e31 ansible/awx_web:latest "/tini -- /bin/sh -c." 12 minutes ago Up 12 minutes 0.0.0.0:80->8052/tcp awx_web 641b42ab536f memcached:alpine "docker-entrypoint.s." 18 minutes ago Up 18 minutes 11211/tcp memcached b333012d90ac rabbitmq:3 "docker-entrypoint.s." 19 minutes ago Up 19 minutes 4369/tcp, 5671-5672/tcp, 25672/tcp rabbitmq ada52935513a postgres:9.6 "docker-entrypoint.s." 19 minutes ago Up 19 minutes 5432/tcp postgres [ installer]#
AWX가 준비되었으며 브라우저에서 액세스할 수 있습니다.
사용자 이름은 "admin"이고 비밀번호는 "password"입니다.
AWX 서버에서 비밀번호 없는 로그인 구성
3개의 호스트 모두에서 사용자를 생성합니다. 3개 서버 모두에서 아래 단계를 따르십시오.
[ ~]# useradd ansible [ ~]# useradd ansible [ ~]# useradd ansible
ssh 키 생성:
[ ~]# su - ansible [ ~]$ ssh-keygen Generating public/private rsa key pair. Enter file in which to save the key (/home/ansible/.ssh/id_rsa): Created directory '/home/ansible/.ssh'. Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /home/ansible/.ssh/id_rsa. Your public key has been saved in /home/ansible/.ssh/id_rsa.pub. The key fingerprint is: SHA256:j30gyTVQxcWIocdKMbVieZvfJzGkCjXhjtc5qu+fE8o The key's randomart image is: +---[RSA 2048]----+ | +o==.+. | | O.oo . | | * @ . | | + @ * + | | S * = o | | B =.o o | | ..=.o.o .| | .E... o | | .oo.o. | +----[SHA256]-----+ [ ~]$
3개 서버 모두에 sudoers 항목을 파일의 마지막 항목으로 추가합니다.
[ ~]# visudo ansible ALL=(ALL) NOPASSWD: ALL
id_rsa.pub의 콘텐츠를 3개 서버 모두의 authorized_keys에 복사합니다.
[ .ssh]$ cat id_rsa.pub ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC4QmuzjVnGUnT1o6xGXD3DCDPUMiTf0xUkOU4kYrkpxHYZ1nWG1MBNGWChyWobnTKYDh4c80+ftSyPHAdeV6KOwADOu6MXvMXHMK3EDe4jn+R0ZArQTEF2qKSBgve23wQu5IoqdWjvBoIEGqxw3LkYbdGxZ5dqKlP5ePkRKal4TncV+tlhueDaKz8QfvXgz+y2jc3HMWAH6a7UYsDKutDttmDDVUwfMcvoS9j2VYOUHkTCenx/2Y3296ULmWCREW9e6fTXLmOowIBDAar01CThmAzYCnBDNAFOsolh9dL1CKwLCvOyK1UBgJlfrzdGI/+fS7aFiaqhXpt6hI4xndJf [ .ssh]$ pwd /home/ansible/.ssh [ ~]$ cat .ssh/authorized_keys ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC4QmuzjVnGUnT1o6xGXD3DCDPUMiTf0xUkOU4kYrkpxHYZ1nWG1MBNGWChyWobnTKYDh4c80+ftSyPHAdeV6KOwADOu6MXvMXHMK3EDe4jn+R0ZArQTEF2qKSBgve23wQu5IoqdWjvBoIEGqxw3LkYbdGxZ5dqKlP5ePkRKal4TncV+tlhueDaKz8QfvXgz+y2jc3HMWAH6a7UYsDKutDttmDDVUwfMcvoS9j2VYOUHkTCenx/2Y3296ULmWCREW9e6fTXLmOowIBDAar01CThmAzYCnBDNAFOsolh9dL1CKwLCvOyK1UBgJlfrzdGI/+fS7aFiaqhXpt6hI4xndJf [ ~]$chmod 600 .ssh/authorized_keys
클라이언트1
[ ~]# su - ansible [ ~]$ ls [ ~]$ mkdir .ssh [ ~]$ cat .ssh/authorized_keys ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC4QmuzjVnGUnT1o6xGXD3DCDPUMiTf0xUkOU4kYrkpxHYZ1nWG1MBNGWChyWobnTKYDh4c80+ftSyPHAdeV6KOwADOu6MXvMXHMK3EDe4jn+R0ZArQTEF2qKSBgve23wQu5IoqdWjvBoIEGqxw3LkYbdGxZ5dqKlP5ePkRKal4TncV+tlhueDaKz8QfvXgz+y2jc3HMWAH6a7UYsDKutDttmDDVUwfMcvoS9j2VYOUHkTCenx/2Y3296ULmWCREW9e6fTXLmOowIBDAar01CThmAzYCnBDNAFOsolh9dL1CKwLCvOyK1UBgJlfrzdGI/+fS7aFiaqhXpt6hI4xndJf [ ~]$ chmod 700 .ssh [ ~]$ chmod 600 .ssh/authorized_keys
클라이언트2
[ ~]# su - ansible [ ~]$ ls [ ~]$ mkdir .ssh [ ~]$ cat .ssh/authorized_keys ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC4QmuzjVnGUnT1o6xGXD3DCDPUMiTf0xUkOU4kYrkpxHYZ1nWG1MBNGWChyWobnTKYDh4c80+ftSyPHAdeV6KOwADOu6MXvMXHMK3EDe4jn+R0ZArQTEF2qKSBgve23wQu5IoqdWjvBoIEGqxw3LkYbdGxZ5dqKlP5ePkRKal4TncV+tlhueDaKz8QfvXgz+y2jc3HMWAH6a7UYsDKutDttmDDVUwfMcvoS9j2VYOUHkTCenx/2Y3296ULmWCREW9e6fTXLmOowIBDAar01CThmAzYCnBDNAFOsolh9dL1CKwLCvOyK1UBgJlfrzdGI/+fS7aFiaqhXpt6hI4xndJf [ ~]$ chmod 700 .ssh [ ~]$ chmod 600 .ssh/authorized_keys
키리스 로그인 확인:
[ .ssh]$ ssh client1 The authenticity of host 'client1 (192.168.1.21)' can't be established. ECDSA key fingerprint is SHA256:TUQNYdF4nxofGwFO7/z+Y5dUETVEI0xPQL4n1cUcoCI. ECDSA key fingerprint is MD5:5d:73:1f:64:0e:03:ac:a7:7b:33:76:08:6d:09:90:26. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added 'client1,192.168.1.21' (ECDSA) to the list of known hosts. Last login: Sun Mar 4 13:39:33 2018 [ ~]$ exit logout Connection to client1 closed. [ .ssh]$ [ .ssh]$ ssh client2 The authenticity of host 'client2 (192.168.1.22)' can't be established. ECDSA key fingerprint is SHA256:7JoWzteeQBwzc4Q3GGN+Oa4keUPMca/jtqv7gmmEZxg. ECDSA key fingerprint is MD5:85:77:3a:a3:07:31:d4:c1:41:ed:30:db:74:b4:ce:67. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added 'client2,192.168.1.22' (ECDSA) to the list of known hosts. Last login: Sun Mar 4 13:51:27 2018 [ ~]$ exit logout Connection to client2 closed. [ .ssh]$
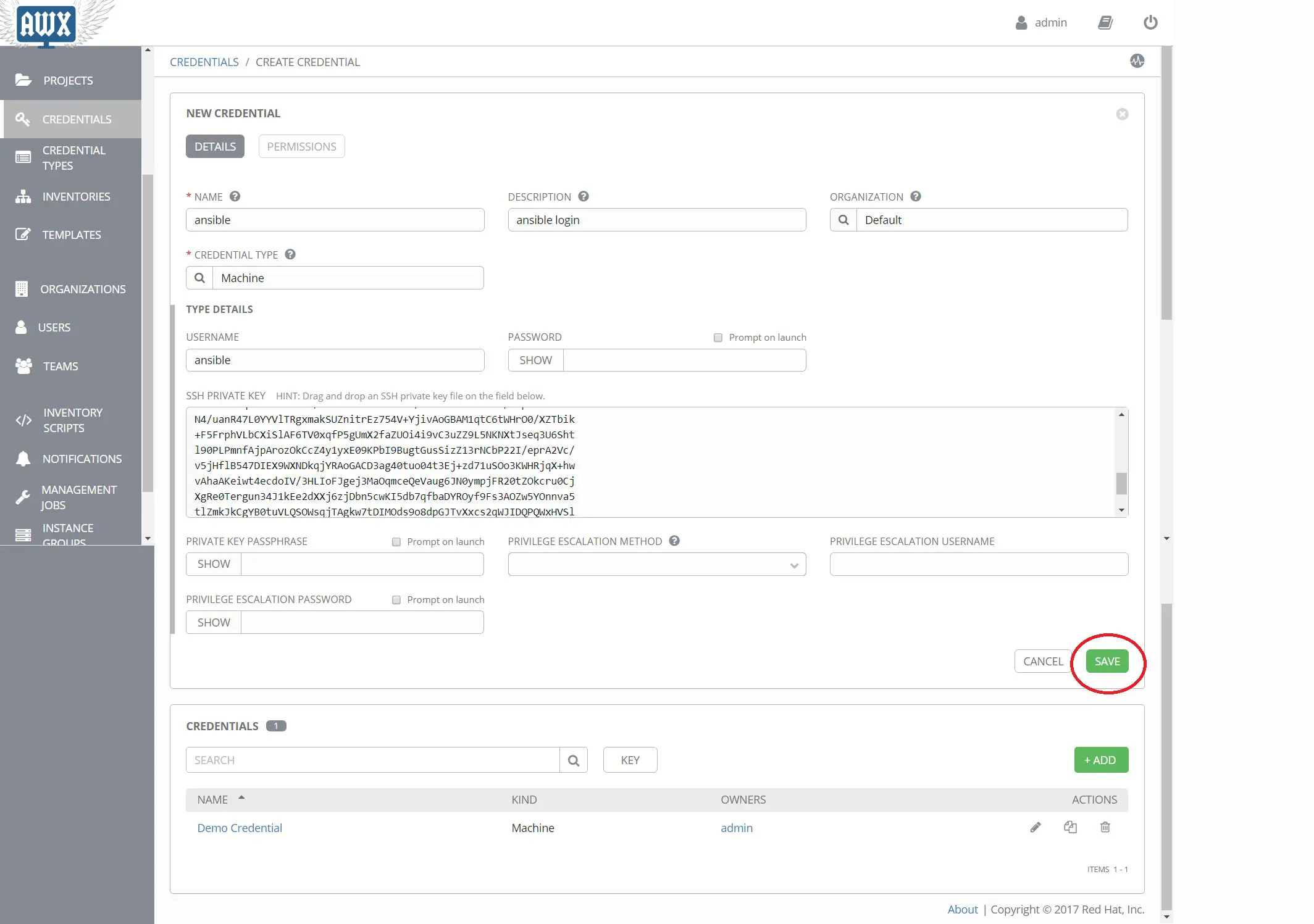
이제 이 아이콘을 클릭하고 자격 증명 -> 추가로 이동합니다.
조직을 선택하고 사용자 이름과 설명을 입력합니다.
여기서 사용자 이름은 \ansible\입니다.

자격 증명 유형에서 머신을 선택하고 세부 정보를 입력합니다.
AWX 서버에서 비공개 키를 가져옵니다.
[ .ssh]$ pwd /home/ansible/.ssh [ .ssh]$ cat id_rsa id_rsa id_rsa.pub [ .ssh]$ cat id_rsa -----BEGIN RSA PRIVATE KEY----- MIIEpAIBAAKCAQEAuEJrs41ZxlJ09aOsRlw9wwgz1DIk39MVJDlOJGK5KcR2GdZ1 htTATRlgoclqG50ymA4eHPNPn7UsjxwHXleijsAAzrujF7zFxzCtxA3uI5/kdGQK 0ExBdqikgYL3tt8ELuSKKnVo7waCBBqscNy5GG3RsWeXaipT+Xj5ESmpeE53FfrZ Ybng2is/EH714M/sto3NxzFgB+mu1GLAyrrQ7bZgw1VMHzHL6EvY9lWDlB5Ewnp8 f9mN9velC5lgkRFvXun01y5jqMCAQwGq9NQk4ZgM2ApwQzQBTrKJYfXS9QisCwrz sitVAYCZX683RiP/n0u2hYmqoV6beoSOMZ3SXwIDAQABAoIBAQCcfiUU6S9fJfca DTmqxHrcIyJJzZDN3GvvSRBaDNLwa2BWz3Mf4Z+1m6Ebp4IME/W9ePgQZIGyxeAj Z43Gja2Nifrlmi2JYpWjeG+MvLwN26XfSHx6rtlGmzKkoIQc98qIvSevqepGYAOa 0sC0VnKKEfNvtei+jVam4hy/e9/oQWHV8c/yueLWpCx2pWOy5m7WVLdwNQSK+8pu sxHLFTNCSC9wddBN80FVxhJQ7L4D2DzcprhcfUz6Uz7Ju7v8MtSksirDnaGliWJ3 NvxhntJYKvgQ30pvBr//y0lYnAB+O0jJhOpHlgD2hNSlI8sgUxmVyl+gC9Dhnq+v 1uKm3CThAoGBAOx+YIGGT/ymqJ53k8Dj4keKctI4+E3p/7Tr2jEyRff177VUjITQ UnrRTw1W+XSE5cszitVYbv0WUwTJoSSrKaRaVG7iORaqcv0LkG8gnlcrcifRXSl5 5xMsPCw0adwtoyhrHQLbENntMl+iQw2JbE6fvldvNe2kPdL3B2T7Jw1RAoGBAMd1 GvsOHLaKtTD0me+wgGnql0GIp90elE7rQ1p6VMxZkE68b+0jX9xHAt2zxocR84+L Gi6uAZvBqnwmH48c7Do6/oulrJXH2OcT6S8+F/kM7PWNT0Z0J0MW/+npVoPwSihZ N4/uanR47L0YYVlTRgxmakSUZnitrEz754V+YjivAoGBAM1qtC6tWHrO0/XZTbik +F5FrphVLbCXiSlAF6TV0xqfP5gUmX2faZUOi4i9vC3uZZ9L5NKNXtJseq3U6Sht l90PLPmnfAjpArozOkCcZ4y1yxE09KPbI9BugtGusSizZ13rNCbP22I/eprA2Vc/ v5jHflB547DIEX9WXNDkqjYRAoGACD3ag40tuo04t3Ej+zd71uSOo3KWHRjqX+hw vAhaAKeiwt4ecdoIV/3HLIoFJgej3MaOqmceQeVaug6JN0ympjFR20tZOkcru0Cj XgRe0Tergun34J1kEe2dXXj6zjDbn5cwKI5db7qfbaDYROyf9Fs3AOZw5YOnnva5 tlZmkJkCgYB0tuVLQSOWsqjTAgkw7tDIMOds9o8dpGJTvXxcs2qWJIDQPQWxHVSl Qimh5DFBkrNDAYKKC386KaZOEKwG7G1YuGbh1+ns3piscJaBi2lPaeA1Y/QA6pCT t9Hbdzre5x0gDbKSHOk+QLJkVdfQX9jamRE6W0k0pXVF6ur8N5zfxA== -----END RSA PRIVATE KEY----- [ .ssh]$
개인 키(예제).
-----BEGIN RSA PRIVATE KEY----- MIIEpAIBAAKCAQEAuEJrs41ZxlJ09aOsRlw9wwgz1DIk39MVJDlOJGK5KcR2GdZ1 htTATRlgoclqG50ymA4eHPNPn7UsjxwHXleijsAAzrujF7zFxzCtxA3uI5/kdGQK 0ExBdqikgYL3tt8ELuSKKnVo7waCBBqscNy5GG3RsWeXaipT+Xj5ESmpeE53FfrZ Ybng2is/EH714M/sto3NxzFgB+mu1GLAyrrQ7bZgw1VMHzHL6EvY9lWDlB5Ewnp8 f9mN9velC5lgkRFvXun01y5jqMCAQwGq9NQk4ZgM2ApwQzQBTrKJYfXS9QisCwrz sitVAYCZX683RiP/n0u2hYmqoV6beoSOMZ3SXwIDAQABAoIBAQCcfiUU6S9fJfca DTmqxHrcIyJJzZDN3GvvSRBaDNLwa2BWz3Mf4Z+1m6Ebp4IME/W9ePgQZIGyxeAj Z43Gja2Nifrlmi2JYpWjeG+MvLwN26XfSHx6rtlGmzKkoIQc98qIvSevqepGYAOa 0sC0VnKKEfNvtei+jVam4hy/e9/oQWHV8c/yueLWpCx2pWOy5m7WVLdwNQSK+8pu sxHLFTNCSC9wddBN80FVxhJQ7L4D2DzcprhcfUz6Uz7Ju7v8MtSksirDnaGliWJ3 NvxhntJYKvgQ30pvBr//y0lYnAB+O0jJhOpHlgD2hNSlI8sgUxmVyl+gC9Dhnq+v 1uKm3CThAoGBAOx+YIGGT/ymqJ53k8Dj4keKctI4+E3p/7Tr2jEyRff177VUjITQ UnrRTw1W+XSE5cszitVYbv0WUwTJoSSrKaRaVG7iORaqcv0LkG8gnlcrcifRXSl5 5xMsPCw0adwtoyhrHQLbENntMl+iQw2JbE6fvldvNe2kPdL3B2T7Jw1RAoGBAMd1 GvsOHLaKtTD0me+wgGnql0GIp90elE7rQ1p6VMxZkE68b+0jX9xHAt2zxocR84+L Gi6uAZvBqnwmH48c7Do6/oulrJXH2OcT6S8+F/kM7PWNT0Z0J0MW/+npVoPwSihZ N4/uanR47L0YYVlTRgxmakSUZnitrEz754V+YjivAoGBAM1qtC6tWHrO0/XZTbik +F5FrphVLbCXiSlAF6TV0xqfP5gUmX2faZUOi4i9vC3uZZ9L5NKNXtJseq3U6Sht l90PLPmnfAjpArozOkCcZ4y1yxE09KPbI9BugtGusSizZ13rNCbP22I/eprA2Vc/ v5jHflB547DIEX9WXNDkqjYRAoGACD3ag40tuo04t3Ej+zd71uSOo3KWHRjqX+hw vAhaAKeiwt4ecdoIV/3HLIoFJgej3MaOqmceQeVaug6JN0ympjFR20tZOkcru0Cj XgRe0Tergun34J1kEe2dXXj6zjDbn5cwKI5db7qfbaDYROyf9Fs3AOZw5YOnnva5 tlZmkJkCgYB0tuVLQSOWsqjTAgkw7tDIMOds9o8dpGJTvXxcs2qWJIDQPQWxHVSl Qimh5DFBkrNDAYKKC386KaZOEKwG7G1YuGbh1+ns3piscJaBi2lPaeA1Y/QA6pCT t9Hbdzre5x0gDbKSHOk+QLJkVdfQX9jamRE6W0k0pXVF6ur8N5zfxA== -----END RSA PRIVATE KEY-----
ssh 개인 키에서 개인 키를 복사하고 저장을 클릭하십시오.
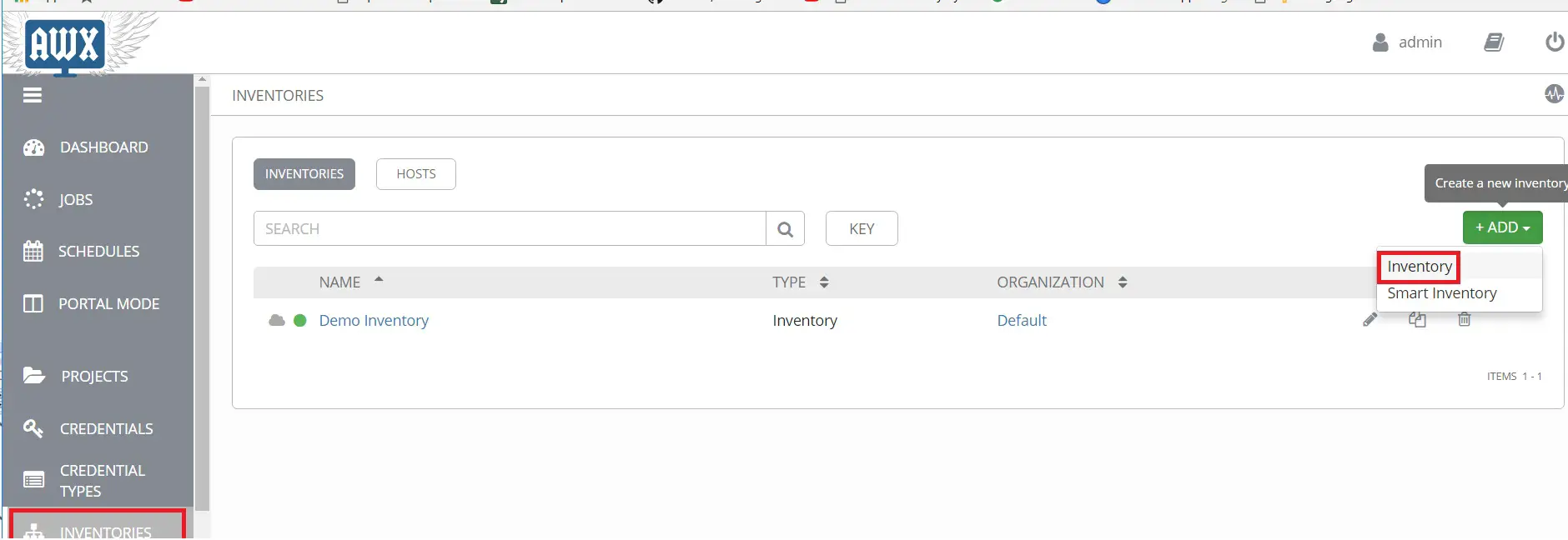
인벤토리를 클릭하고 인벤토리 추가를 클릭합니다.
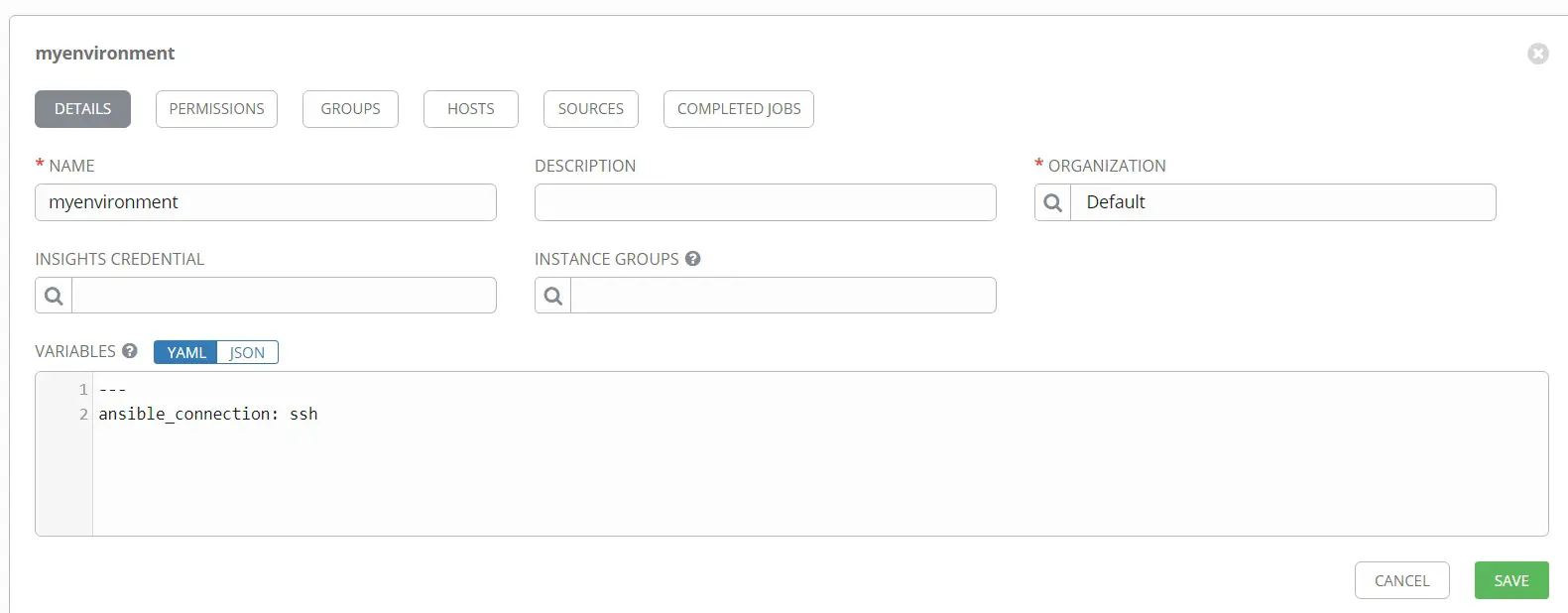
그에 따라 세부 사항을 채우십시오.
호스트 -> 호스트 추가를 클릭합니다.
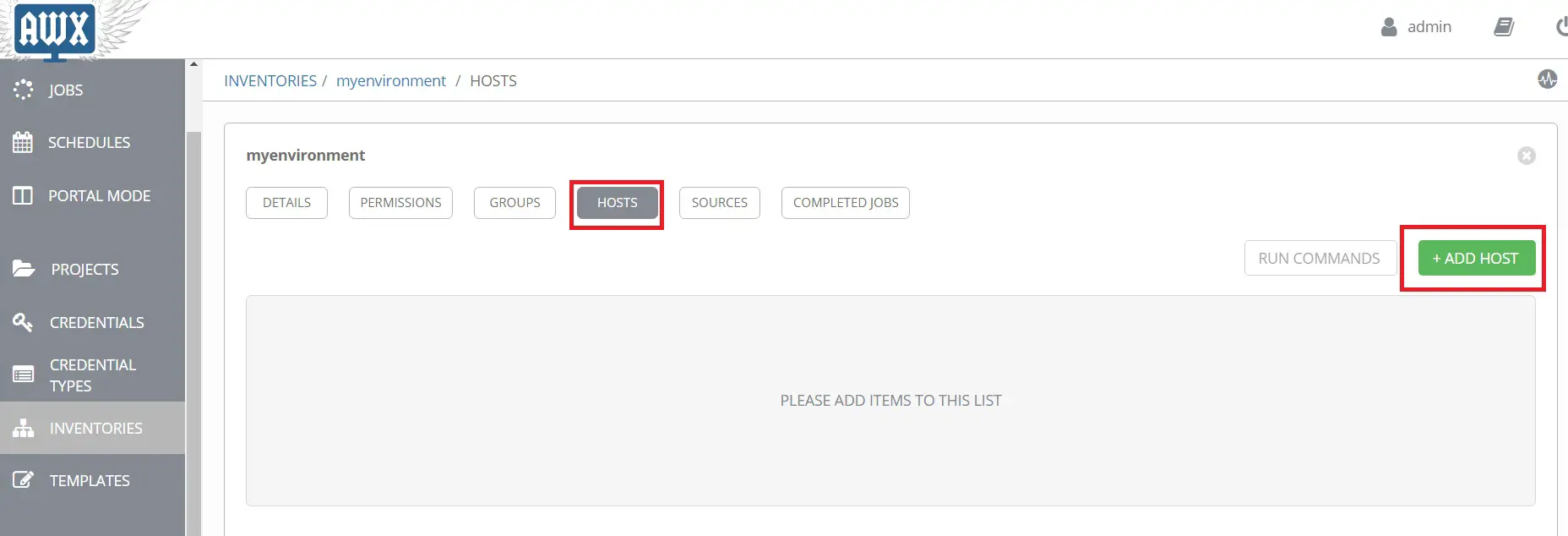
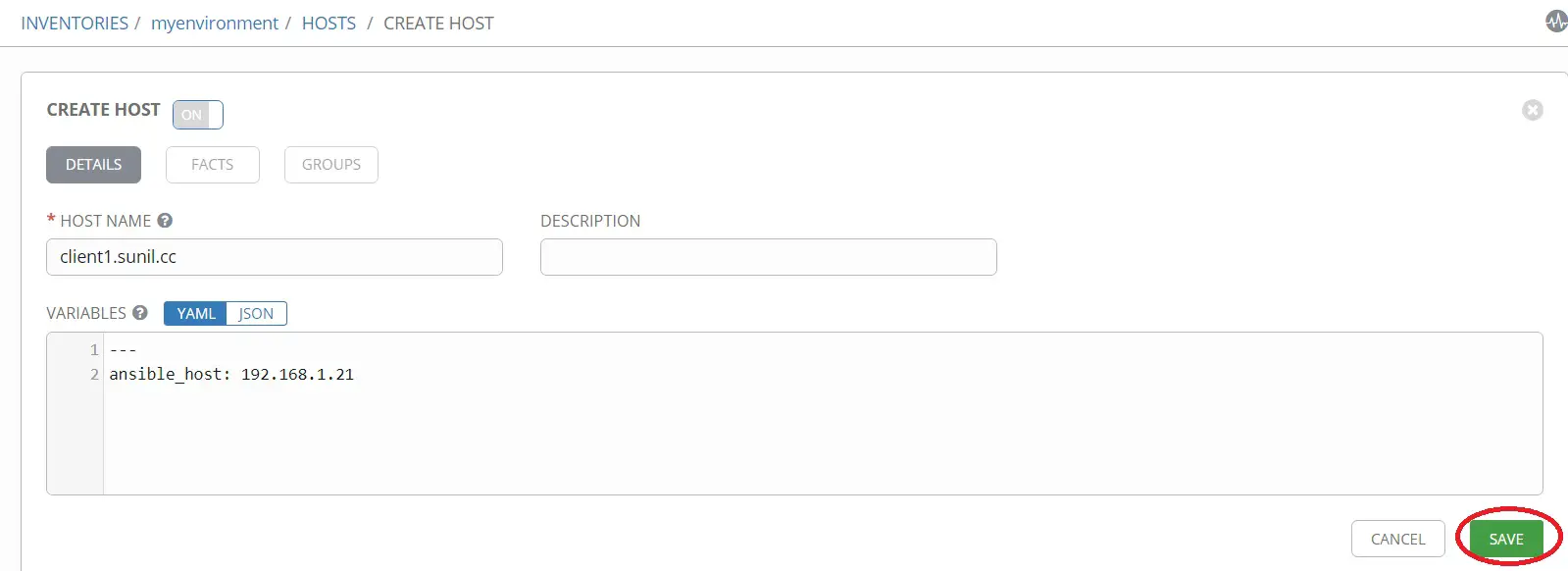
아래 세부 정보를 추가합니다.
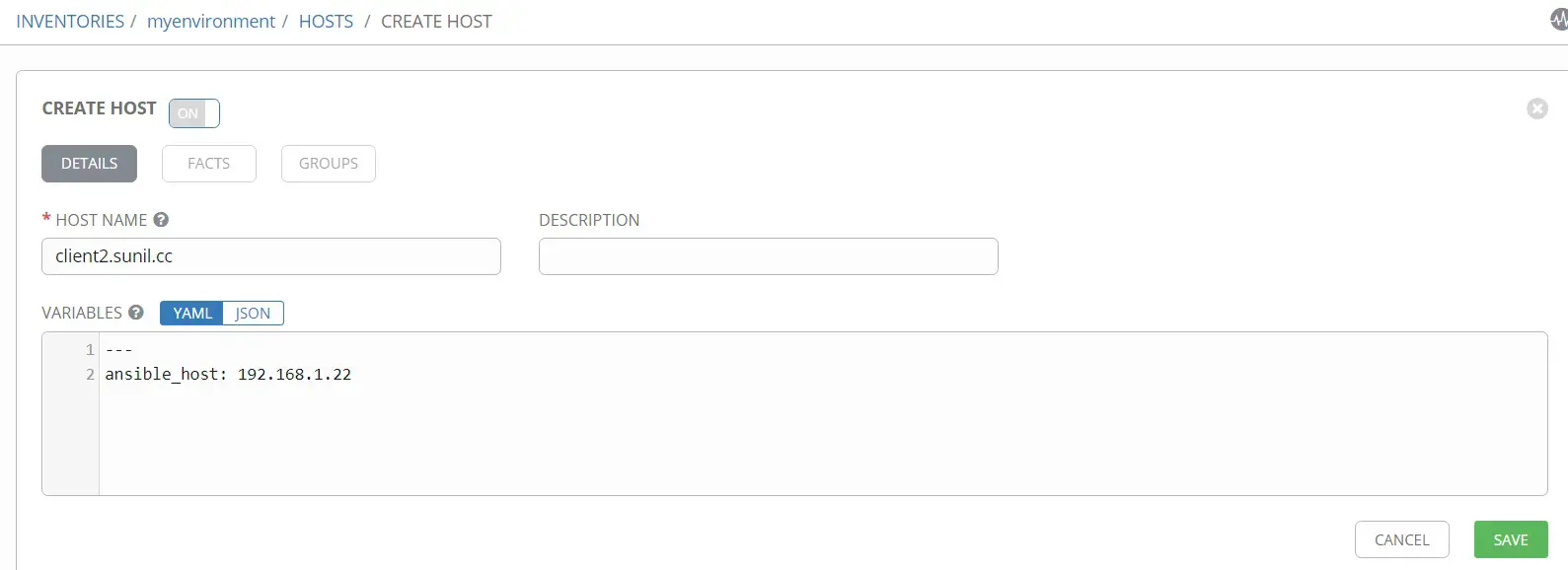
client2에 대해 아래 세부 정보를 추가합니다.
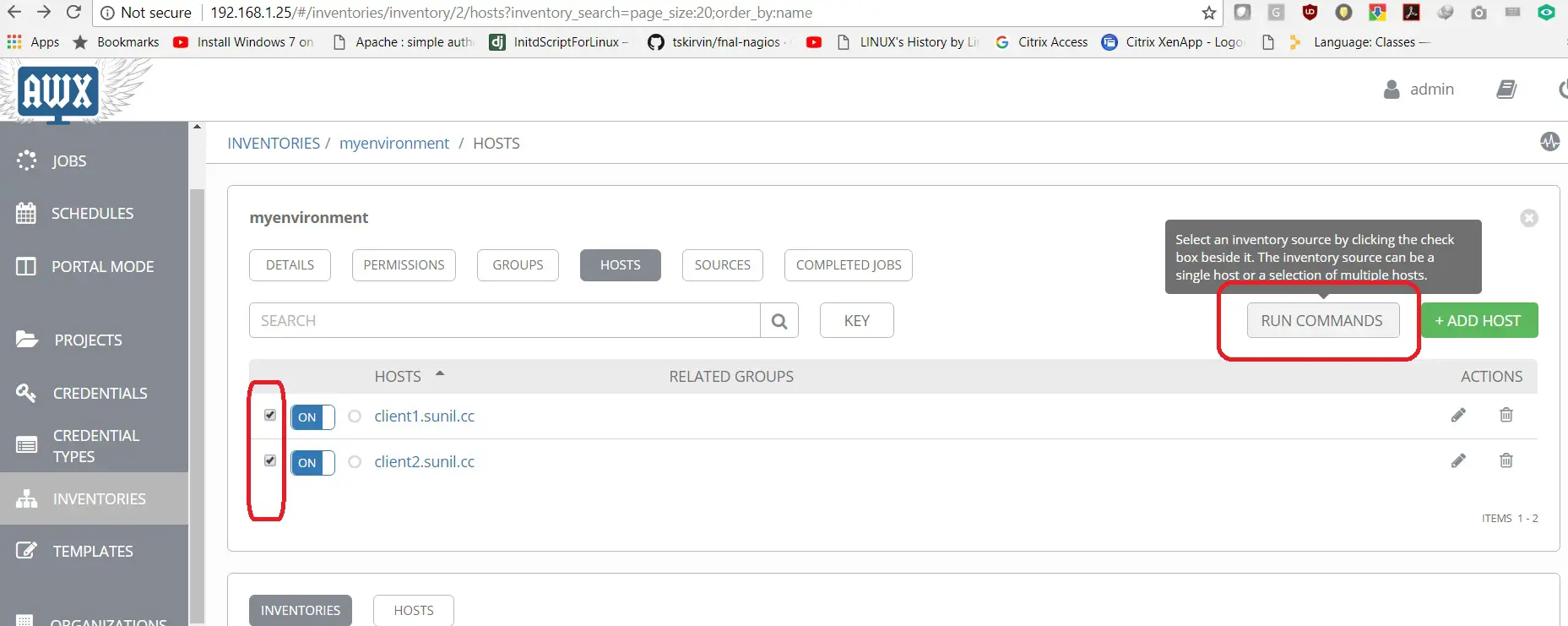
AWX를 통해 연결을 테스트합니다.
두 호스트를 모두 선택하고 명령 실행을 클릭하십시오.
ping 및 기타 세부 정보를 선택하고 실행을 클릭합니다.
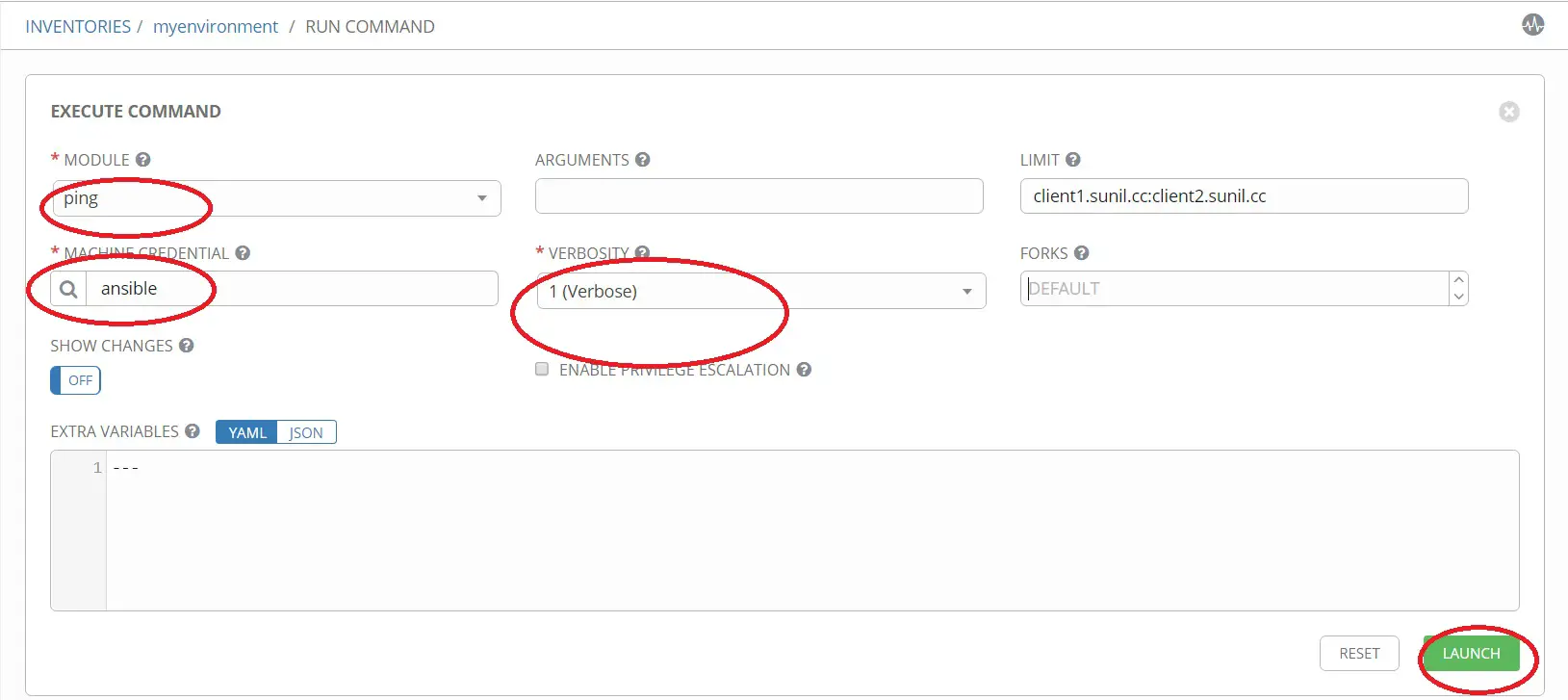


이것이 이 튜토리얼의 전부입니다. 다음 튜토리얼에서 rpm을 통해 AWX를 설치하는 방법과 플레이북을 실행하는 방법, 추가 튜토리얼에서 API 호출을 수행하는 방법을 보여드리겠습니다.
참조
- https://github.com/ansible/awx/blob/devel/INSTALL.md
- http://docs.ansible.com/ansible-tower/latest/html/quickstart/index.html